Compliance Shortcuts That End Up Hurting CMMC Requirements Long-Term
Shortcuts might save time now, but when it comes to compliance, they often cause bigger problems later. Businesses trying to meet CMMC requirements sometimes cut corners without realizing the long-term risks. Whether it’s using generic policies or outdated security tools, these mistakes can lead to costly fixes, compliance failures, and increased vulnerability. Here are some common shortcuts that can do more harm than good.
Using Generic Security Policies That Don’t Align with CMMC-specific Controls
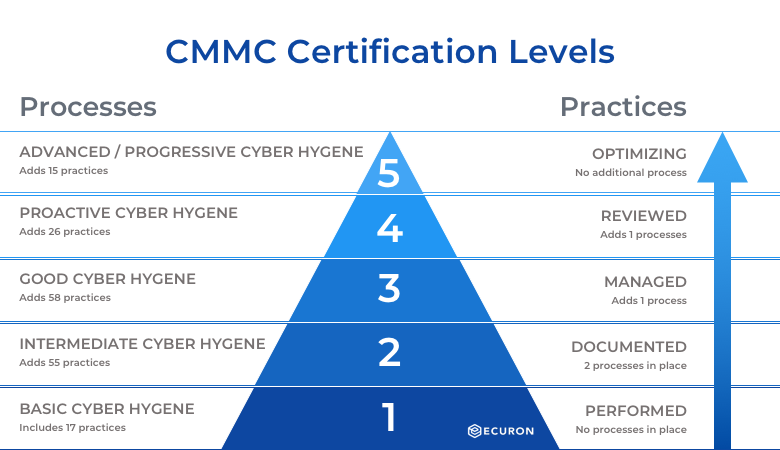
Security policies shouldn’t be a copy-and-paste job. Many companies rely on generic templates that don’t fully align with CMMC compliance requirements, thinking they’re good enough. While these policies may look complete, they often lack the details necessary to meet the specific controls required for CMMC level 1 requirements and CMMC level 2 requirements. Without proper alignment, businesses risk non-compliance during an audit.
CMMC security controls require more than broad statements about cybersecurity practices. They demand detailed procedures outlining access controls, data protection, and incident response plans tailored to specific security requirements. Policies need to be mapped to each required practice, ensuring they reflect the real-world security measures the company follows. Without this, businesses could find themselves scrambling to update their policies after an audit exposes weaknesses.
Relying on Outdated or Free Security Tools That Lack Proper Threat Detection
Free security tools may seem like a cost-effective solution, but they often lack the advanced detection and response capabilities needed to meet CMMC requirements. Many of these tools are limited in their ability to detect modern threats, leaving gaps in security that bad actors can exploit. Relying on outdated software also puts businesses at risk, as older tools may no longer receive updates or security patches.
For CMMC compliance requirements, organizations must ensure their security tools provide real-time threat detection, logging, and response capabilities. This means investing in solutions that go beyond basic antivirus software. Security tools should include robust monitoring, multi-factor authentication, and endpoint protection. Without these, companies leave themselves open to breaches, potentially failing to meet CMMC level 2 requirements.
Skipping Regular Risk Assessments Assuming Past Compliance Means Future Security
A past compliance audit doesn’t guarantee future security. Some organizations assume that because they met CMMC requirements once, they don’t need frequent risk assessments. This is a dangerous mindset. Threats evolve, and without regular evaluations, security gaps can go unnoticed until it’s too late.
Risk assessments should be an ongoing process, not a one-time event. Regular evaluations help identify weaknesses, assess new threats, and ensure compliance remains intact. Businesses must test security controls, update policies based on findings, and address vulnerabilities before they become major issues. CMMC level 2 requirements emphasize continuous improvement, meaning companies must consistently adapt their security posture.
Ignoring the Need for an Experienced Cybersecurity MSSP to Handle Complex Security Layers
Managing CMMC compliance requirements isn’t a simple task. Some businesses try to handle everything in-house, only to realize too late that they lack the expertise to navigate complex security layers. Without an experienced cybersecurity MSSP, organizations may struggle to implement and maintain the necessary security controls.
An MSSP brings expertise in monitoring threats, securing sensitive data, and ensuring compliance with evolving CMMC level 2 requirements. They provide continuous oversight, threat detection, and incident response, ensuring businesses remain compliant without overwhelming internal teams. Ignoring the need for professional support often results in compliance failures and security risks that could have been avoided.
Thinking One-size-fits-all Policies Will Cover CMMC Forever
Cybersecurity policies aren’t set in stone. Some organizations believe that once policies are written, they never need to be changed. This approach can lead to outdated policies that no longer align with current CMMC requirements. Compliance expectations evolve, and failing to update policies can leave businesses exposed to new risks.
CMMC compliance requirements require policies to be reviewed and updated regularly. As security threats change, businesses must adjust their policies to address emerging vulnerabilities. Companies should conduct routine policy reviews, ensuring their security measures remain relevant. A flexible approach to policy management is the best way to maintain compliance and protect sensitive data.
Ignoring System Hardening Because “It’s Not a Requirement”
System hardening often gets overlooked because it’s not explicitly listed as a CMMC requirement. However, failing to secure systems properly makes it easier for attackers to exploit weaknesses. Unpatched software, default settings, and unnecessary services create security risks that could lead to compliance failures.
Hardening systems involves disabling unnecessary features, applying security patches, and implementing strict access controls. While CMMC level 2 requirements don’t mandate system hardening directly, many security controls depend on it. Businesses that skip this step expose themselves to threats that could have been prevented. A secure system is a compliant system, and ignoring hardening is a shortcut that often leads to bigger problems down the road.



